
What is a keylogger, and what can it do?
As you may know from the name itself, a keylogger is just software (unless it’s a hardware keylogger) that monitors, records, and sends data to third parties. Usually, this is done without your knowledge, resulting in data and identity theft. Over a while, keyloggers have evolved in functionality and the ability to track, record a range of your activities that could seriously harm you. The list below includes, but is not limited to, the capabilities of most modern keyloggers. Software (unless it is a hardware keylogger) monitors, records, and sends data to third parties. Usually, this is done without your knowledge, resulting in data and identity theft. Over some time, keyloggers have evolved to be functional and able to track and record a series of your activities that could seriously harm you. The list below includes, but is not limited to, the capabilities of most modern key recorders.
- Keep the user invisible so that they cannot view or uninstall it.
- Track keyboard and mouse activity
- Control various system settings without user knowledge (usually with administrative privileges)
- Monitor the operation of files and folders Active files and folders
- Capture login details of email accounts, bank accounts, and other online and offline accounts
- Track clipboard activities of Clipboard activities
- Control your microphone and webcam
- Capture screenshots of your screen activities on desktop
- Send collected data via FTP, LAN, email, etc.
Protect yourself from Keylogging
To protect yourself from keylogger software, you can use anti-keylogger software like GhostPress, which encrypts all of your keystrokes. The nice thing about GhostPress is that it’s free, compact, and portable, which makes it the right choice when you want to use a public computer or a system that isn’t yours can use anti-keylogger software.
To get started, visit the official website and download the software. After downloading, extract the contents of the zip file. Once downloaded, remove the contents of the zip file.
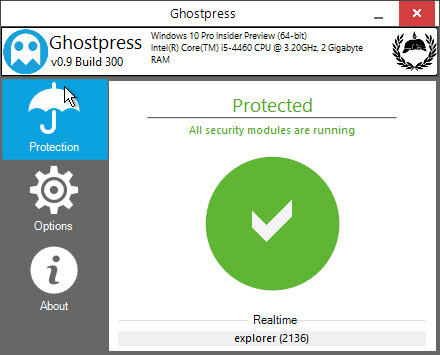
Now, execute the EXE file in the directory. As a portable application, you don’t need to install it. Once the application has been launched, it will automatically encrypt any key presses. You don’t need to mess with any of the settings.
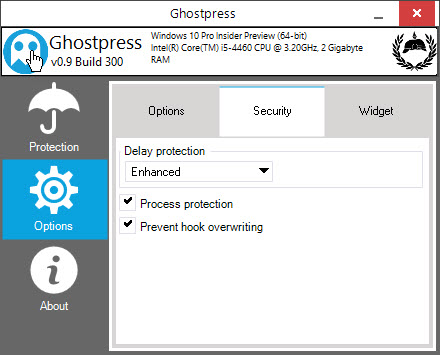
If you want to add extra protection, you can do so by simply selecting “Options” that appear on the left panel and then navigating to the “Security” tab. Here, check the checkbox “Process Protection” and option, set the Delay Protection to “Enhanced”. When the Delay Protection option is enabled, all of your keystrokes will be randomly delayed for a short time so that keylogger software cannot detect who you are based on your typing behavior. You can’t see who you are based on your typing behavior.
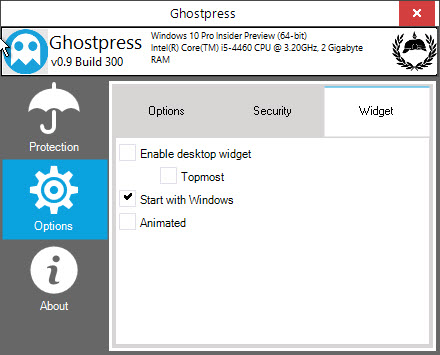
If you want to use this software on your computer regularly, then navigate to the tab “Widgets” and select the checkbox “Start with Windows”. When enabled, GhostPress automatically launches at system boot, no need to manually establish each time. Software on your computer, then navigate to the “Widgets” tab and select the “Get Started with Windows ” checkbox. When enabled, GhostPress automatically launches at system boot, with no need to start manually every time.
Suppose you want more advanced protection against webcam robbery, system screenshots, remote access, clipboard robbery, etc. In that case, you need to see high-end software like Zemana AntiLogger, Robbery, etc., then you need to look at insurance software such as Zemana AntiLogger.
All the software you use can only protect you from the keylogger software. If the attacker used a hardware keylogger between the keyboard and the system, your keys could still be leaked. So be extra cautious when you can use a public computer like in internet cafes. The software you use can only protect you from keylogger software. If the attacker used the hardware keylogger between the keyboard and the system, keys could still be leaked. So be extra cautious when you can use a public computer like in internet cafes.





